Do You Need Cyber Insurance for Your Digital Assets?
The Direct Costs of a Cyberattack
Direct costs associated with cyberattacks encompass a wide range of expenses, from the immediate disruption of operations to the long-term damage to reputation and customer trust. These costs can be substantial and often underestimated. For example, the recovery process after a ransomware attack can involve significant expenses for decryption tools, forensic analysis, and data restoration, often exceeding the initial ransom demand. Furthermore, lost productivity during downtime and the necessity of hiring cybersecurity experts to assess and mitigate the damage further contribute to the direct financial burden.
Beyond the immediate financial hit, the costs associated with regulatory fines and legal fees can quickly escalate. Compliance failures, data breaches, and subsequent penalties from governing bodies can cripple a company's financial stability, potentially leading to significant financial losses beyond the initial attack.
Damage to Reputation and Customer Trust
A successful cyberattack can irreparably damage a company's reputation and erode customer trust. The loss of sensitive customer data, such as credit card information or personal details, can lead to substantial legal liabilities and reputational damage. News of a breach often spreads rapidly online, affecting a company's public image and deterring potential customers. The long-term effects on brand loyalty and future sales can be devastating, requiring significant investment in rebuilding trust and brand perception.
The aftermath of a cyberattack can severely impact a company's public image, leading to a loss of credibility and the potential for a decline in customer loyalty. This damage can be long-lasting and difficult to repair, requiring considerable effort and resources to restore public confidence.
Lost Revenue and Decreased Productivity
Cyberattacks frequently result in significant losses of revenue and decreased productivity. Downtime caused by a breach can halt operations, leading to lost sales and missed opportunities. The time and resources spent on incident response, recovery, and remediation further reduce productivity and profitability. In addition, the fear of future attacks can negatively impact employee morale and motivation, exacerbating the damage to operational efficiency.
Operational Disruption and Recovery Costs
The operational disruption caused by a cyberattack can be extensive and costly. Systems may be compromised, data may be encrypted or stolen, and critical processes may be halted. The recovery process often involves significant costs, including the time and resources needed to restore systems, rebuild data, and implement enhanced security measures. The disruption can also lead to the loss of valuable customer data, requiring significant investments in rebuilding trust and ensuring compliance with regulations.
Financial Impact on Employees and Stakeholders
The financial fallout of a cyberattack can extend beyond the company itself. Employees may face loss of income or benefits if the company suffers financial setbacks. Investors may lose confidence in the company's future prospects, leading to a decline in stock value. The ripple effects of a cyberattack can be felt across various stakeholders, impacting their financial well-being and potentially creating long-term economic instability.
The Long-Term Implications and Prevention Strategies
The long-term implications of cyberattacks extend far beyond the immediate financial losses. A breach can damage a company's reputation, impact investor confidence, and create a culture of fear and distrust within the organization. Effective prevention strategies, including robust cybersecurity measures, incident response plans, and employee training, are crucial to mitigating the risk of future attacks. Proactive measures can significantly reduce the financial and reputational damage associated with cyberattacks.
Analyzing data allows businesses to understand consumer preferences and trends related to freshness, enabling them to proactively adjust their offerings and strategies. This proactive approach can lead to increased customer satisfaction and loyalty as consumers are presented with products that meet their expectations regarding freshness. By identifying patterns in sales data, businesses can anticipate demand fluctuations, optimize inventory management, and reduce waste. This data-driven approach fosters a more efficient and effective operation.
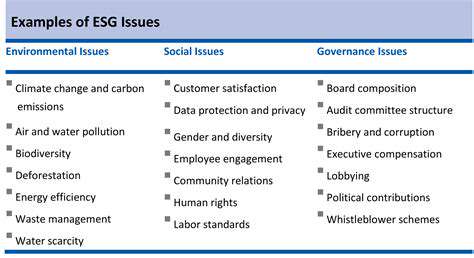
Beyond the Basics: What Types of Cyber Insurance Policies Exist?
Beyond the Fundamentals of Data Analysis
Data analysis goes far beyond simply crunching numbers. It involves a deep dive into understanding the context, identifying trends, and drawing meaningful conclusions from the data. This process requires a keen eye for detail and a strong understanding of the data's origins and the questions it can answer. A solid foundation in statistical methods is crucial, but equally important is the ability to communicate findings effectively to diverse audiences.
Effective data analysis requires careful consideration of various factors, including data quality, appropriate methodologies, and the potential for bias. This comprehensive approach ensures that the insights derived from the data are both accurate and actionable. It also involves staying up-to-date with the latest advancements in the field to leverage the most powerful analytical tools available.
Exploring Diverse Data Types
Data comes in many forms, from structured numerical data to unstructured text and images. Understanding these different types and their respective characteristics is essential for selecting the appropriate analytical techniques. Successfully applying the right methods to the right data yields the most impactful results.
Structured data, like sales figures or customer demographics, is relatively straightforward to analyze. However, unstructured data, such as social media posts or customer reviews, demands more sophisticated approaches to extract valuable information. Techniques like natural language processing (NLP) and image recognition play a crucial role in unlocking the insights hidden within these forms of data.
Techniques for Advanced Analysis
As data sets grow larger and more complex, traditional methods might prove insufficient. Advanced analytical techniques, such as machine learning and deep learning, become essential for extracting meaningful patterns and insights. These methods allow us to uncover hidden relationships and predict future outcomes with greater accuracy.
Machine learning algorithms can identify complex patterns in large datasets, while deep learning models can learn intricate representations from images and text. These techniques are revolutionizing various industries, enabling more precise predictions and more efficient decision-making.
The Role of Visualization in Data Understanding
Visualizing data is crucial for conveying complex information in a clear and concise manner. Visual representations, such as charts, graphs, and dashboards, transform raw data into easily digestible insights. This visual representation makes it easier to identify trends and patterns, facilitating faster comprehension of the data's story.
Effective visualizations not only help in understanding the data but also in communicating findings to stakeholders. Choosing the right visualization method is key to effectively conveying the insights derived from the analysis. Interactive dashboards allow users to explore the data dynamically, enabling deeper understanding and more insightful decision-making.
Ethical Considerations in Data Analysis
Data analysis, while powerful, comes with ethical responsibilities. Maintaining data privacy and ensuring responsible use of findings are paramount. The potential for bias in data and algorithms must be carefully considered and addressed. Transparency in the analytical process is vital to build trust and maintain ethical standards throughout the entire data lifecycle.
Data security and privacy regulations must be adhered to rigorously. Data should be anonymized or aggregated whenever possible to protect individuals' privacy. Understanding and mitigating potential biases in datasets is crucial to avoid perpetuating or amplifying harmful stereotypes or inequalities.
The Cost-Benefit Analysis: Is Cyber Insurance Worth the Investment?

Understanding the Financial Implications
A thorough cost-benefit analysis of cybersecurity measures is crucial for any organization, large or small. This assessment must meticulously evaluate the potential financial losses from a cyberattack, encompassing direct costs like data recovery, system restoration, and legal fees, as well as indirect costs such as reputational damage, lost productivity, and disruption of business operations. Understanding these potential financial impacts is paramount to justifying the investment in robust cybersecurity solutions.
Calculating the return on investment (ROI) for security investments is essential. This calculation considers the projected savings against the costs of implementing various security measures. A well-structured analysis will highlight the long-term financial viability of cybersecurity investments, demonstrating how they can safeguard assets and contribute to overall profitability.
Assessing the Risks and Vulnerabilities
Identifying and assessing the organization's vulnerabilities is a vital first step in a cost-benefit analysis. This involves a comprehensive review of existing security protocols, systems, and data. Understanding the specific risks associated with each vulnerability is critical to prioritize security investments. This analysis should include a clear understanding of the potential impact of various cyberattacks, such as ransomware, phishing, and malware attacks.
A detailed risk assessment should consider the likelihood and potential impact of each threat. This allows for the prioritization of security measures based on their potential impact on the organization.
Evaluating Security Solutions and Their Costs
The next step is to evaluate various security solutions and their associated costs. This includes evaluating different types of software, hardware, and services, considering factors such as licensing fees, maintenance costs, training requirements, and implementation complexity. Carefully comparing different solutions is essential to identify the most effective and cost-effective options to address specific vulnerabilities.
A critical aspect of this step is the assessment of the ongoing operational costs. This includes the human resources required for managing security tools, regular security updates, and incident response planning. Thorough research is key to identifying solutions that align with the organization's budget and operational requirements.
Calculating the Expected Benefits
A critical component of the analysis is projecting the potential benefits of implementing security measures. This involves estimating the reduction in the likelihood of successful cyberattacks and the minimized financial impact of an attack. Quantifying the potential savings from reduced downtime, data recovery costs, and legal fees is essential.
Determining the potential increase in operational efficiency and customer trust is also a key benefit that must be factored into the analysis. This component requires a realistic assessment of the expected positive outcomes of security implementation.
Read more about Do You Need Cyber Insurance for Your Digital Assets?
Hot Recommendations
- Understanding Fundamental Analysis in Investing
- Understanding Risk Management in Investing
- Guide to Rebalancing Your Portfolio
- Best Investment Strategies for Beginner Investors
- Best Budgeting Methods Compared
- How to Use Dollar Cost Averaging
- How to Budget When You Hate Budgeting
- Understanding the Efficient Market Hypothesis
- Guide to Retirement Planning for Business Owners
- How to Choose Insurance for a Classic Car
![Best Homeowners Insurance Companies [2025 Review]](/static/images/30/2025-05/TopTierHomeownersInsuranceProvidersin2025.jpg)